

Privacy is now a hot topic on the minds of every technology leader, for one very compelling reason: On January 1, 2020, the California Consumer Privacy Act (CCPA) went into effect.
Like the EU’s Global Data Privacy Regulation (GDPR), the new law brings stronger protections around the information businesses collect about California residents, as well as new mandates for organizations that collect such data. The CCPA is just the first of what could be dozens of new privacy laws enacted throughout the country.
For our CIO Insight call late last year we were privileged to be joined by three experts in the field of privacy:
These gentlemen discussed what the new privacy legislation means for enterprises, how organizations can adapt to this new regulatory environment, and the emerging discipline of Privacy Ops.
The CCPA was in part a response the 2017 Equifax data breach that exposed the personal information of more than 140 million Americans. It was formulated in 2018, the same year GDPR went into effect and Facebook’s Cambridge Analytica scandal made headlines. Consumers were ready for more consumer privacy protections and, as is often the case in regulatory matters, California was leading the way.
The CCPA grants several new rights for consumers, including the right to know what personally identifiable information (PII) has been collected about them and how it’s being used, as well as the right to opt out of the sale of PII and to delete it. It also expands the definition of PII to include IP addresses, browser and search histories, geolocation, biometric information, and any other data that could be reasonably linked, directly or indirectly, with a particular consumer or household.
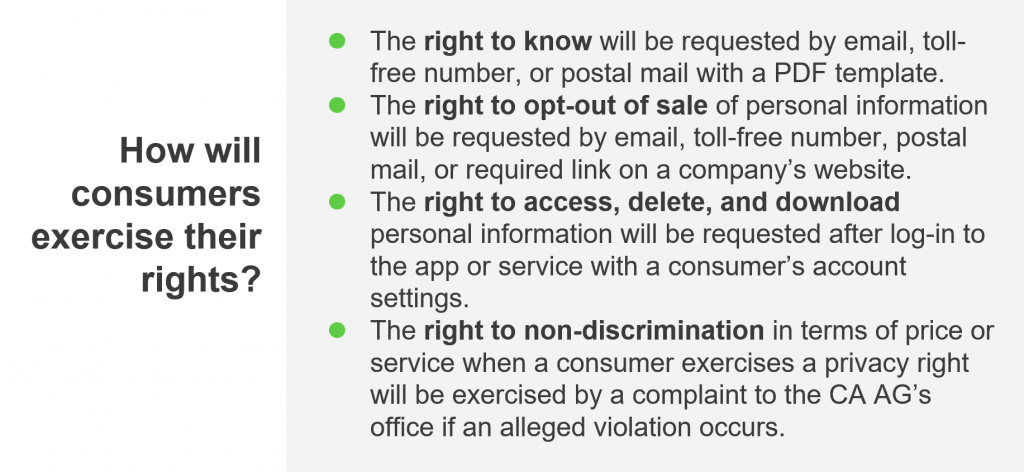
Individuals who believe an organization has violated their rights under the CCPA can sue for up to $750 per violation. The California State Attorney General can also levy fines up to $2500 or $7500 per violation, depending on whether the act was intentional.
The impact of CCPA will extend far beyond the borders of California. There are already copycat laws enacted or pending in 18 other states, some stricter than California’s. There are also half a dozen proposed privacy bills at the federal level, though none are likely to pass in the foreseeable future.
According to PwC, enterprises have already spent more than $5 million on average preparing for the CCPA, with spending expected to rise dramatically throughout 2020.
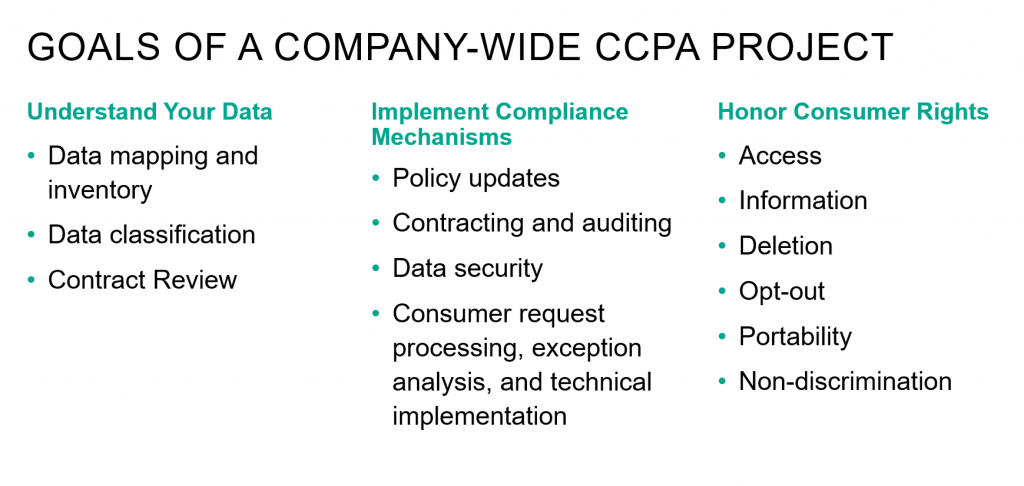
The first thing every business needs to do is determine whether they fall under the jurisdiction of the law. The CCPA applies to any enterprise that a) collects consumer information and has annual revenues of $25 million or more; b) collects personal data from at least 50,000 consumers, households, or devices; or c) derives more than half of its income from the sale of personal information. This includes any subsidiaries or divisions that fall under this definition, even if the larger organization does not.
Businesses will need to identify the types of information they collect and whether they fit into one or more of the 11 data categories broadly defined within the law. They also need to determine if that information falls under the CCPA’s list of exemptions. These include organizations that collect personal information governed by other statutes, such as HIPAA, GLBA, or the Drivers Privacy Act, to name a few. Partial exemptions also exist for information collected about employees, as well as in certain B2B transactions.
Companies need to prepare for lawsuits that will come as a result of the CCPA. That will result in dramatic changes in how organizations implement and document cybersecurity processes and vulnerabilities. They will need to seriously consider performing assessments under the protection of attorney-client privilege to avoid opening themselves up to more litigation.
McDermott, Will, & Emery is spending a lot of time right now thinking about how we’re going to defend those cases. If our clients get breached you can be sure we’ll have our folks studying the path of attack and fixing the issues that contributed to it. We’ll be coming forward with sworn declarations from security professionals saying that we have responded to the incident, corrected all the issues, and in our view the security program that was in place before was reasonable.
Most important, organizations need to anticipate issues that could arise as a result of the CCPA and come up with strategies to address them. And they need to think about a program that can scale, because they’re likely to encounter regulations even more stringent than California’s.
As with major shifts in technology, the emergence of strong privacy regulation represents a business opportunity. SECURITI.ai, a recent Mayfield portfolio investment that emerged from stealth mode in August, aims to reduce the complexities of privacy compliance.
Privaci, the company’s full-stack Privacy Ops automation tool, creates a framework enterprises can use to comply with the CCPA, GDPR, and other new global regulations as they arise.
Using AI, Privaci can discover all the personal information a company has collected from each consumer, whether the data is stored in on-premise databases, the cloud, or SaaS applications. It can then help organizations securely manage and automate opt-out and deletion requests.
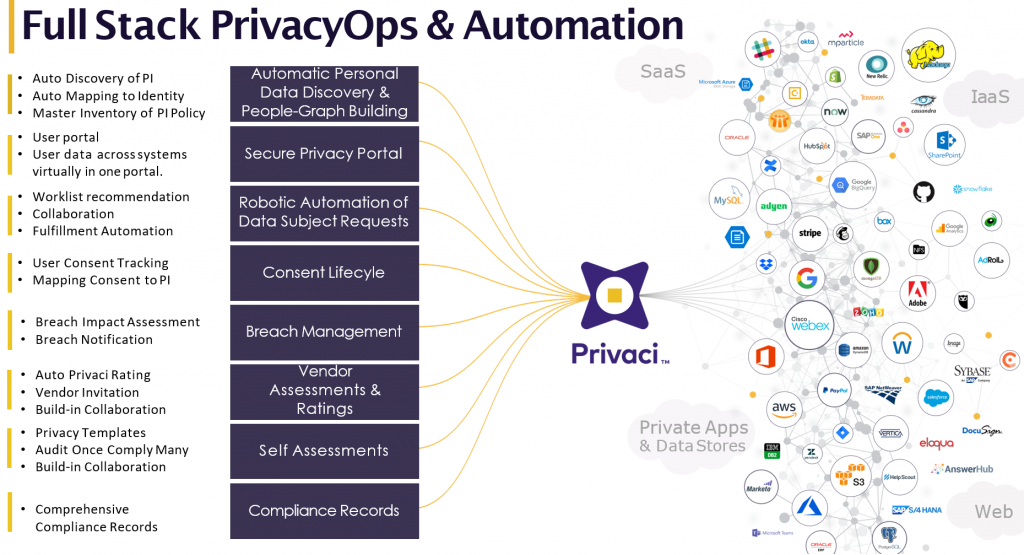
By mapping individuals to the data that’s associated with them, Privaci can greatly simplify the notification process in the event of a data breach. It also allows enterprises to assess the data-handling capabilities and risk potential of third-party vendors, and logs all activities to demonstrate compliance with regulatory requirements.
Perhaps most importantly, Privaci does not require specialized expertise to use. You can communicate with the system using common English phrases, and it will guide you to where the data is sitting and help you fulfill data subject requests (DSRs). Because the cost of fulfilling a single DSR manually can range from $1500 to tens of thousands of dollars, enterprises will want to automate as much of this process as possible.

A Privacy Ops framework is where you can bring all your legal, compliance, IT, and security teams together in one place. You can use it to manage your vendors, data, DSRs, compliance workflows, consent information, and notifications from a single dashboard with full visibility.
The fact you’re a B2B entity doesn’t change the overall assessment of whether the CCPA applies to your business. But it is relevant to the scope of your compliance program. There’s a partial carve out for information collected in the course of corporate due diligence or when providing goods and services to someone acting on behalf of another business.
It depends on what your BAA says. It’s a contract, so it needs to flow down to your business partner’s obligations. You want to be able to say ‘Hey, we’re sharing this data with you, so you have to help us comply with our obligations by only using data for the purposes we’ve authorized for this business relationship. If someone opts out you need to pull them from your database, if there’s a data breach you’re going to indemnify us,’ and so on. There’s a laundry list of things that should be included in these agreements.
The law generally defines reasonable by reference to a hypothetical reasonable person. In the context of information security that often results in lots of issues for lawyers to argue about. But when it comes to data breaches, there’s always some way to argue that an element in a security program was unreasonable. If there’s a hack attack, you can argue there were things the security team should have done to prevent the attack. Or if employees click on something they shouldn’t have, that the organization should have provided better training for them.
One thing to consider is that you’re not required to provide specific pieces of information if exposing that information would create a risk for that individual, such as their passwords. In terms of searching every nook and cranny in your organization for information, you need to develop a reasonable, defensible approach. I don’t see this coming down to a particular data point that wasn’t disclosed because it was stored in a backup archive. But these are hard questions, and I’m hoping the CCPA will be revised in coming years to speak to them with more clarity.
You set a high water mark. You comply with something that gets you 99 percent of the way there, and you preserve your ability to do less for individuals who make an onerous request that isn’t required under the local law. In general, you come up with a program that complies with the highest level requirements – in the EU that’s GDPR, and in the US that’s the CCPA — and you roll that out.
Yes. It can find anything that’s specified in these regulations. Companies can also define their own fields, such as customer or transaction IDs, purchase histories, and so on. All of that is discoverable and linkable as part of the system.
They’re taking a risk-based approach. We are seeing organizations starting to automate their most critical systems, starting with high priority data. And because class action suits are allowed under the CCPA, breach notification becomes even more important. Automation is absolutely needed at that point, because if a system is compromised, and it takes weeks or months to find out whose data was in that system so you can notify them, you are exposed. With damages up to $750 per person, the total cost of a breach could be very high.
We’ve got a comprehensive ebook available on our website, Privaci.ai, detailing the philosophies behind and best practices for Privacy Ops. And we’re available for one-on-one sessions as needed.
